Table of Contents
Introduction
Digital fraud is increasing day by day, with online payment fraud losses projected to exceed $362 billion globally by 2028, as reported by Juniper Research. Fraudsters use VPNs and proxies to steal sensitive data while hiding their original identity. Businesses' security is exposed to more cyber threats with the growing use of such privacy tools. In this guide, we will explore what these anonymity tools are, how cybercriminals exploit them, and the technical methods (including services like IPGeolocation.io) that can help detect and prevent VPN/Proxy-based fraud.
The Rising Threat of VPN/Proxy Fraud
Online anonymity services can be used for both legitimate and malicious purposes. On one side, they provide internet users with privacy and security, but on the other hand, they are exploited by bad actors for criminal activities. VPNs, residential proxies, and TOR are tools that hide a user's identity. They can make a user appear to be coming from a different location than their actual one. That's how attackers conceal their identity, bypass geo-based restrictions, avoid IP-based threat scoring, and conduct cyberattacks without immediate suspicion. Given the impact of loss after being victimized by these frauds, it is critically important for business owners and online platform handlers to understand these tools and implement robust cyber threat intelligence mechanisms to protect their users and assets.
Understanding Anonymity Tools
There are various technologies that fraudsters use to hide their identity online. Below are some common anonymity tools:
VPNs (Virtual Private Networks)
VPNs route a user's traffic through an encrypted tunnel. They use a remote server to route the traffic while masking the user's real IP address and location. This makes it appear as if the traffic is coming from the VPN server’s location rather than the user’s device. A user, whether legitimate or malicious, can bypass location-based restrictions without their activities being identified.
Proxies
A proxy server acts as a bridge between a user and the website they are trying to access. They might not encrypt the traffic like a VPN does, but they also use a remote server. This conceals the user's original IP address and modifies their actual location. The remote server sends a request to the desired site, gets the response or data, and sends it back to the user while bypassing location-based and IP-based restrictions.
Proxy Types:
There are two types of proxies based on their origin.
Data center Proxy:
Proxy services that utilize servers from cloud providers are known as data center proxies. These proxies are not tied to any Internet Service Providers (ISPs) or residential internet connections. They are fast and cheap, but also easier to detect and block. Data center proxies' IP ranges are blocked because of automated request patterns observed on them. As many users share the same IP Address, there is a risk that they might be blocked at once.
Residential Proxy:
Residential proxies use real human IP addresses, such as from home routers or mobile devices, that are affiliated with an ISP rather than a hosting provider. This is why it is difficult to detect and filter malicious requests coming from residential IPs. A residential proxy network often consists of compromised or P2P-shared devices whose owners may be unaware that their IP is being used. By routing through an actual residential ISP connection, a criminal’s traffic looks more legitimate and can bypass some basic proxy detection measures.
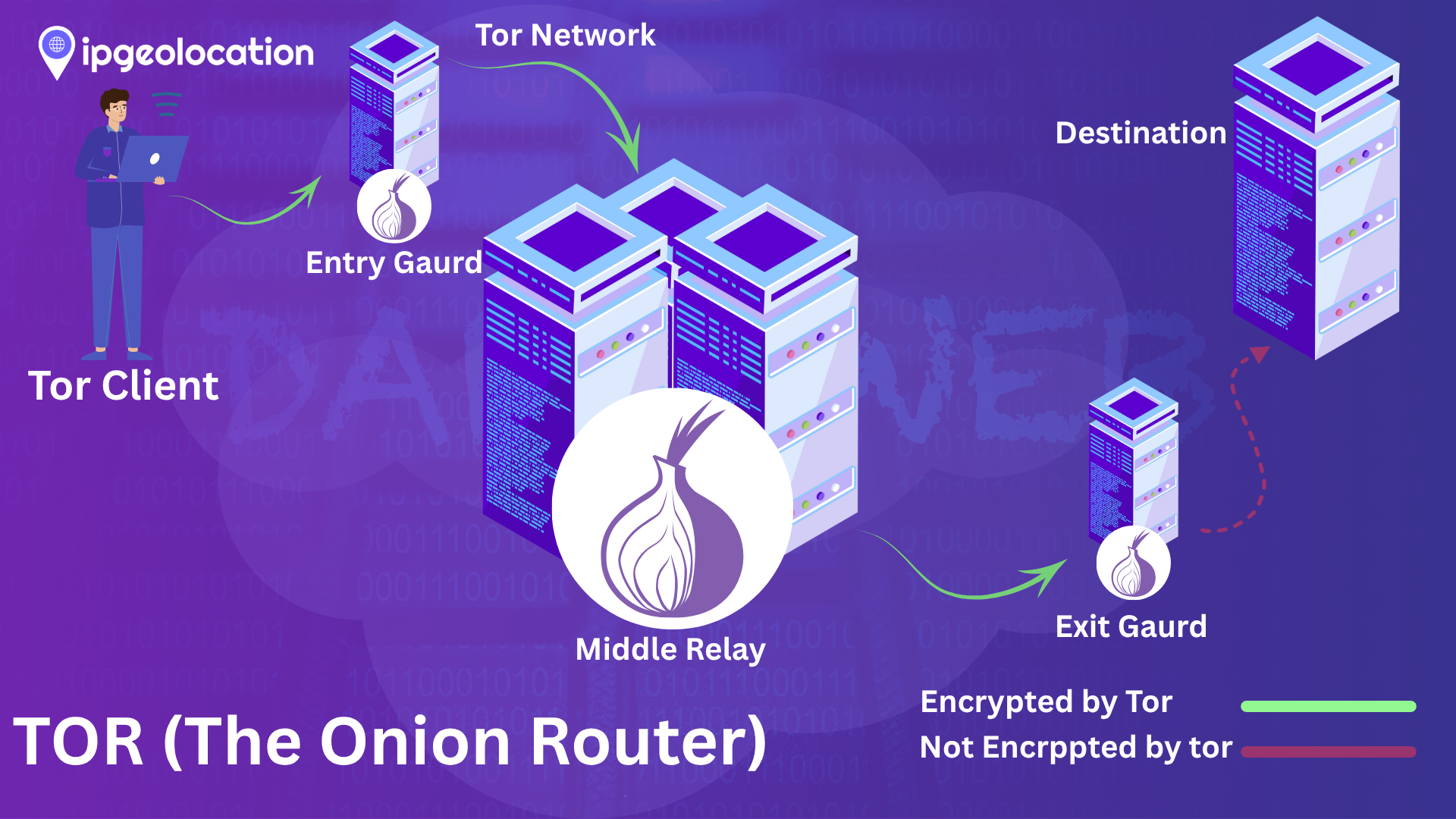
TOR (The Onion Router)
TOR is a specialized network anonymity tool that routes user traffic through multiple volunteered nodes. Encryption is implemented on every layer of the node, making it very difficult to trace the origin of the traffic. Using Tor, a user’s connection is extremely anonymous, appearing to come from the final Tor exit node, which could be anywhere in the world. This high level of anonymity is good for privacy-focused users, but it is also exploited by malicious users on the dark web.
How Fraudsters Exploit VPNs and Proxies
Cybercriminals exploit anonymity tools in many ways to carry out fraud. Here are some main scenarios facilitated by VPNs and proxies:
Account Takeovers (ATOs):
Fraudsters use different methods to get victims' credentials. They may utilize a brute-force technique to crack usernames and passwords. Sometimes they get this sensitive information from data breaches after finding vulnerabilities in security systems. Besides finding technical weaknesses, one more method that exploits human psychology is called phishing. In this technique, attackers disguise themselves as a trusted entity, like a bank, a social media platform, or an IT department. The victims unconsciously click on the sent URL and unknowingly provide their credentials. Attackers perform these activities by hiding themselves behind VPN and proxy networks. An attacker then logs into the victim's account using a proxy server located in the victim's actual location to make their activities less suspicious.
Payment Fraud:
Once criminals have stolen payment information (credit cards, digital wallets, etc.), they use proxies or VPNs to mask their identity during fraudulent transactions. They might first connect through a VPN to “warm up” an e-commerce account by mimicking the victim’s typical browsing patterns to make their activities look less suspicious. They constantly use an IP address from the victim's actual location and a spoofed user-agent to bypass fraud checks that flag location or timezone mismatches. Additionally, fraudsters abuse promotions or bonuses by creating multiple accounts via VPNs/proxies, a tactic known as bonus abuse. By hiding their real IP and location, they can redeem “new user” offers multiple times and violate one-per-customer rules.
Web Scraping and Data Harvesting:
Many automated bots scrape websites for data (pricing, content, or commercial data). Websites often block a single IP that makes too many requests. Fraudsters counter this by using a proxy network in which IP addresses are continuously rotating. If one gets banned, it just switches to another. With a large pool of legitimate IPs, including residential proxies that appear to be different real users, scrapers can distribute requests and avoid detection.
Bot Attacks
Whether it’s credential capturing or running an automated DDoS or spam bot, attackers use VPNs/proxies to optimize their bots. If a bot gets blocked, it simply routes it through a new IP address and continues the attack. In more sophisticated distributed bot attacks, each bot in a network uses a different anonymized IP, making it hard to block them all. Certain proxies (especially residential IP proxies) can even make bot traffic look like ordinary user traffic. This is how attackers bypass IP-based techniques used for fraud prevention.
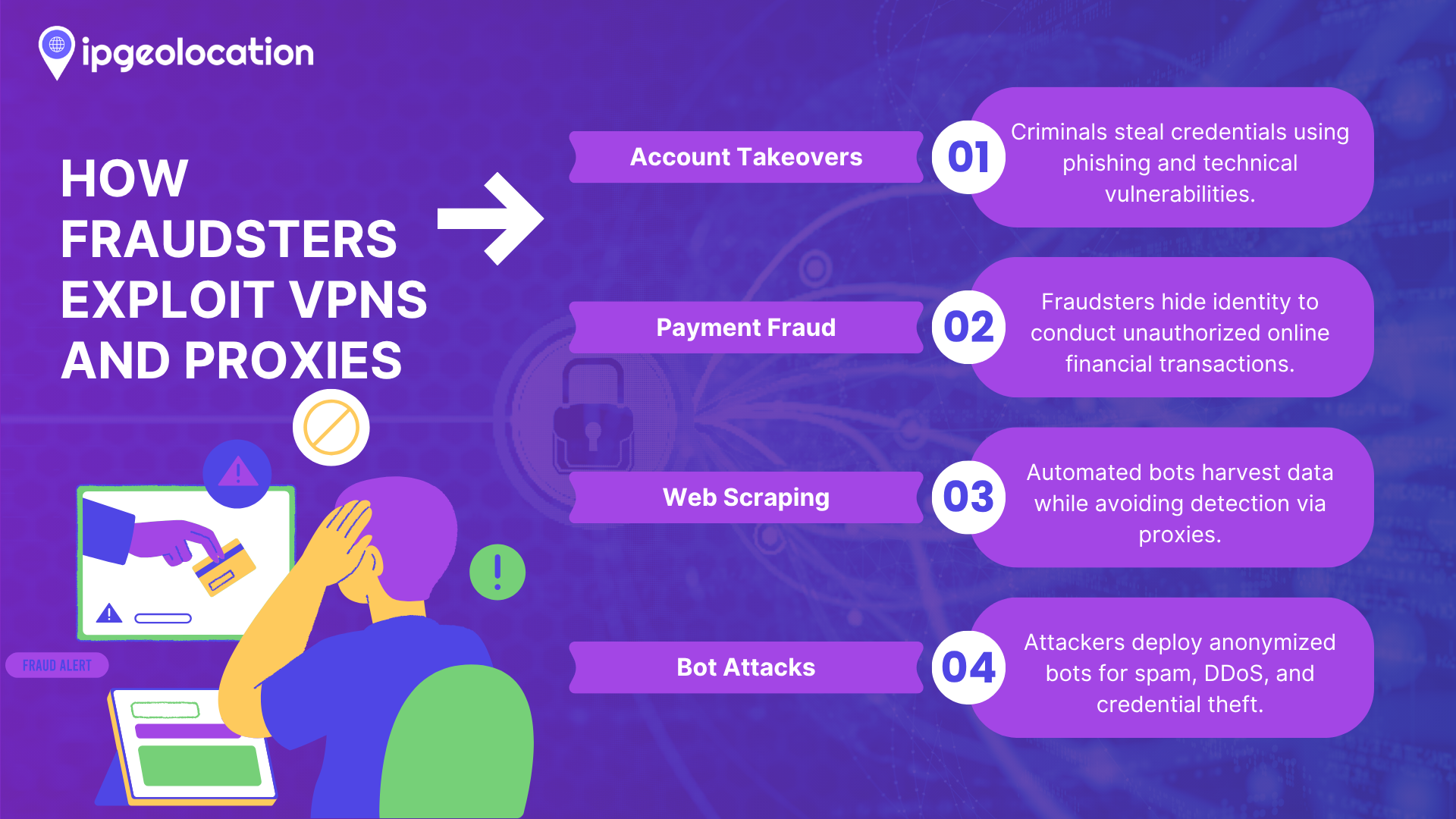
As shown above, anonymity tools are a common source of many forms of fraud, from breaking into accounts, stealing money, and abusing services to attacking systems. The next step for defenders is knowing how to detect when a user is coming through a VPN or proxy, so that extra verification or blocking can be applied. Below, we outline technical methods to spot VPN/proxy usage.
Technical Methods to Detect VPN/Proxy Usage
Detecting VPN or proxy usage is challenging but feasible, especially by combining multiple detection techniques. No single method can guarantee full security (since skilled attackers may bypass one type of check), so it’s best to combine approaches. Here are several technical methods to help identify if a user is coming through an anonymizing service:
Time Zone Consistency Checks:
One of the basic techniques is to compare the visiting users' browser time zone with the time zone of their IP address. If the time zones are not equal, the user is probably using a VPN. However, this technique is not sufficient because the browser's time zone can be spoofed easily. Furthermore, modern privacy-focused browsers tamper with these attributes.
OS Mismatch:
Comparing the device's operating system and the operating system present in the browser helps in detecting VPN usage. The device operating system can also be found by analyzing packets coming from the user's device. If these values are different, most likely the user is connected to VPN.
DNS-Based Detection:
VPNs often funnel not just web traffic but also DNS queries through their own DNS servers to prevent leaks. However, in certain scenarios, DNS leaks occur, where a user’s computer still uses their ISP’s DNS for some lookups. By monitoring DNS requests or performing a DNS leak test via the client, you might catch differences. For instance, if a user’s stated IP is in one country but their DNS requests resolve via an ISP in a different country, that suggests a VPN/proxy user whose real location slipped through via DNS.
Third-Party Detection Services:
Instead of building all checks in-house, many organizations and security teams utilize specialized VPN/proxy detection APIs to handle the challenging task of detecting VPNs and proxies. These services (for example, IPGeolocation.io’s IP Security API) combine multiple intelligence sources to decide if a given IP Address is a VPN, proxy, Tor exit node, a cloud data center, etc. Integrating such services is straightforward. They continue to update their IP reputation database daily to ensure accuracy. It can quickly identify known anonymizer IPs and even score the risk level of an IP (based on factors like whether it’s a hosting provider vs. residential ISP, history of abuse reports, etc.).

IPGeolocation.io’s Role in Providing Cybersecurity Solutions
When it comes to third-party IP intelligence, IPGeolocation.io’s Threat Detection API (also known as the IP Security API) is a powerful option for identifying VPNs, proxies, Tor, and other threats. It offers a comprehensive set of data fields and is continually updated. Here’s how IPGeolocation.io helps developers and security teams protect their platforms:
Comprehensive Threat Data:
For any given IP address, IPGeolocation’s API will tell you if that IP is currently a VPN or proxy server, if it’s a known Tor exit node, or if it’s associated with other threats (like being a bot or part of a spam network). API also provides the VPN/Proxy provider name the user is connected to, which clearly flags it as a consumer VPN service.
Risk Scoring:
Each IP query comes with a threat_score value from 0 to 100, showing the overall risk associated with that IP. This score is computed from various attributes (whether the IP is an anonymizer, a known attacker, in a high-risk data center range, etc.). A higher score means a higher likelihood that the IP is being used for malicious purposes. It's a quick way to evaluate the threat associated with an IP Address, even if it is not VPN, based on its past abusive behavior.
JSON Response Format:
The API returns data in a developer-friendly JSON format. A typical response contains an IP field and a security object with all the relevant flags and info. This makes it easy to integrate into your backend or front-end. You can call the API on each login attempt or transaction, and parse the JSON to get fields like is_proxy, is_tor, proxy_provider, threat_score, etc., then take action in your code (block, log, alert, etc.). Because the response is structured, it’s straightforward to log it or combine it with your own user/session data for further analysis. The response part relevant to security information is given below:
{
"ip": "2.56.188.34",
"security": {
"threat_score": 75,
"is_tor": false,
"is_proxy": true,
"proxy_type": "VPN",
"proxy_provider": "Nord VPN",
"is_anonymous": true,
"is_known_attacker": true,
"is_spam": false,
"is_bot": false,
"is_cloud_provider": true,
"cloud_provider": "Packethub S.A."
}Residential Proxy:
IPGeolocation.io also provides a residential proxy detection database. It includes IP addresses tied to real user devices and ISPs that are used in some malicious activities and are hard to detect. The database not only lists the IP addresses but also provides the last date on which a particular IP was found being used as a proxy. Furthermore, the database is continuously updated to ensure accuracy.
The CSV format for residential proxy data is given below:
start_ip,end_ip,proxy_provider,last_seen
23.134.91.71,23.134.91.71,OXY Labs,2025-06-07
23.134.91.87,23.134.91.87,OXY Labs,2025-06-13
12.252.73.197,212.252.73.197,Evomi Proxy,2025-08-06
212.252.73.199,212.252.73.199,Evomi Proxy,2025-07-13
212.252.69.5,212.252.69.5,Zyte Proxy,2025-08-12
212.252.69.9,212.252.69.9,Zyte Proxy,2025-08-11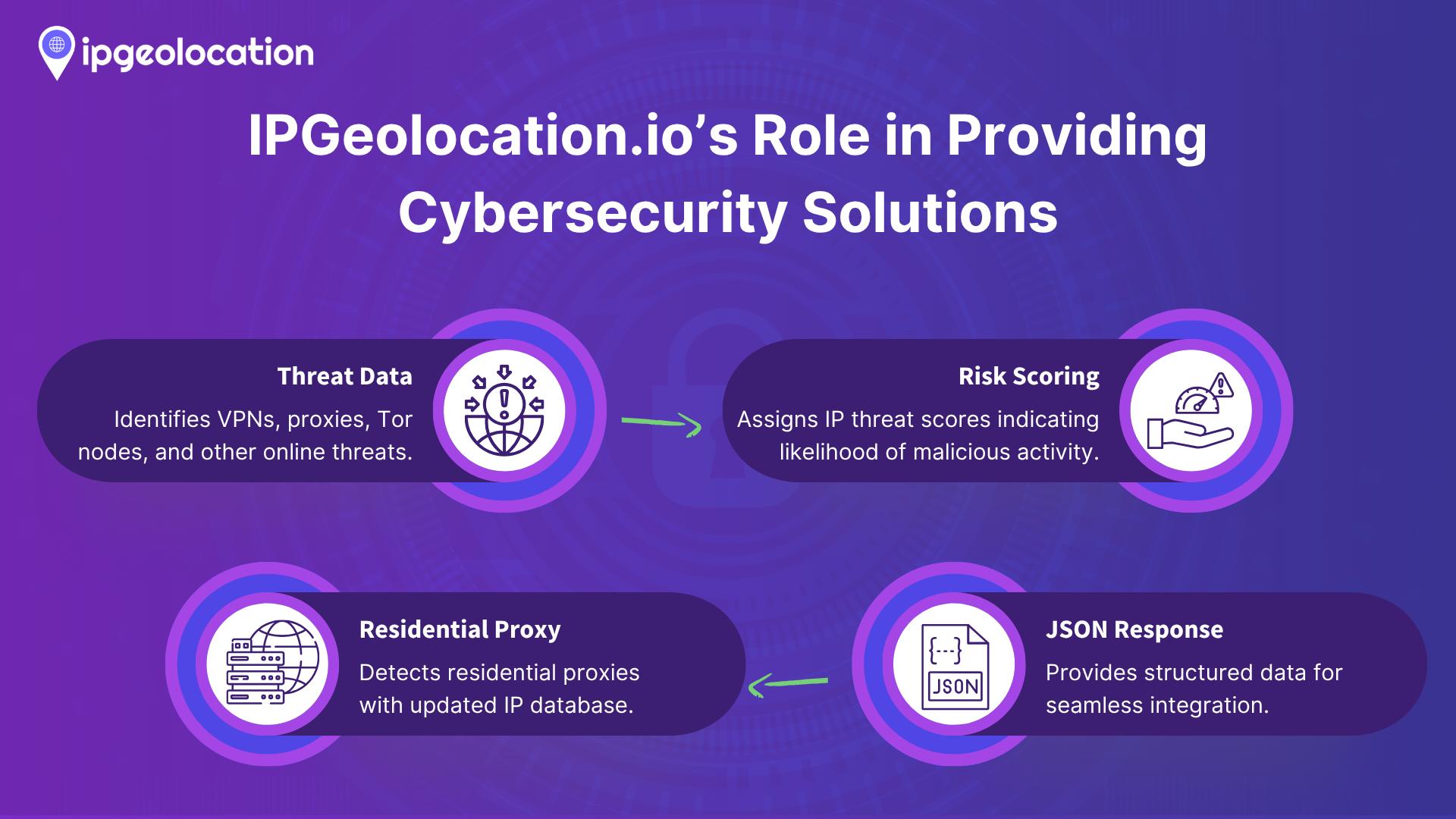
Conclusion
VPNs and proxies are powerful tools. They help in providing privacy and security for ordinary users, but in the wrong hands, they become pathways for cybercriminals. As fraudsters continue to update their hiding techniques and clean their tracks, platforms must stay one step ahead by deploying intelligent detection measures. By combining techniques like IP reputation checks, timezone/DNS consistency tests, and device fingerprinting, along with utilizing up-to-date threat intelligence from services like IPGeolocation.io, businesses can reduce the risk of VPN/proxy-based fraud.
Subscribe Our Newsletter
Get the latest in geolocation tech, straight to your inbox.
Start for
Free
No Credit Card Needed
Access up to 1,000 requests/day with our forever free plan.
Sign Up Free